What is Social Engineering and how to protect your business
What is Social Engineering and how to protect your business
10 NOVEMBER 2016
Category: ICT,Business IT support
Author: Seb Waligorski
What is Social Engineering and how to protect your business
Social engineering
Social Engineering is a method used by hackers to psychologically manipulate people into performing an action or divulging information.
Our Business IT support wanted to share with you a few tips that might save your business.
Introduction
We all know how to spot a suspicious email. It’s obvious to most people, for example, when they receive an email from exiled crown prince of Burundi asking for your help in liberating his millions from the country, that it isn’t wise to click those links, open those attachments, or reply to him to arrange a bank transaction. But it’s precisely because most people are now wise to these kinds of scams that scammers are using much more sophisticated methods. These methods are much more effective than the clumsy, poor quality attempts we’re used to seeing because they are carefully designed not to arouse suspicion. A successful social engineering attempt is one that you won’t even notice happened – you’ll think you just helped a colleague, friend, or family member.

Social engineering exploits can be initiated by email or other messaging services, via websites specifically designed to look like other websites, and by phone. They may even have a physical, face-to-face element. They will often be coordinated to use a few of these methods together (e.g. An email, followed up with a phone call).
PC security is based on imposing restrictions – people, on the other hand, want to help each other overcome obstacles.
There is no straightforward way of identifying a sophisticated social engineering exploit, but here are some examples of what a social engineering exploit might look like:
- A colleague who is known to you (and who is a friend of yours) asks you by email to carry out a bank transfer, as you’ve discussed earlier;
- A colleague asks for account details, relating to something you’ve discussed before;
- A colleague asks to borrow your log-in details because they say they can’t carry out a vital task otherwise, and serious problems will arise if they can’t access the system;
- A colleague asks you to prop the office door open for them because they left their key at home, and they don’t want to cause inconvenience or get into trouble.


If carried out effectively, the request will seem completely normal. Social engineering techniques are effective because they are plausible and believable. Scammers spend time carrying out research to make their contact seem normal.
Social Engineering Methods
(From our Business IT support)
Email spoofing
Spoofing means the faking of an email address to make an email appear as though it came from someone else – usually a trustworthy source. For example, a scammer might spoof an email so that it appears to come from [email protected].
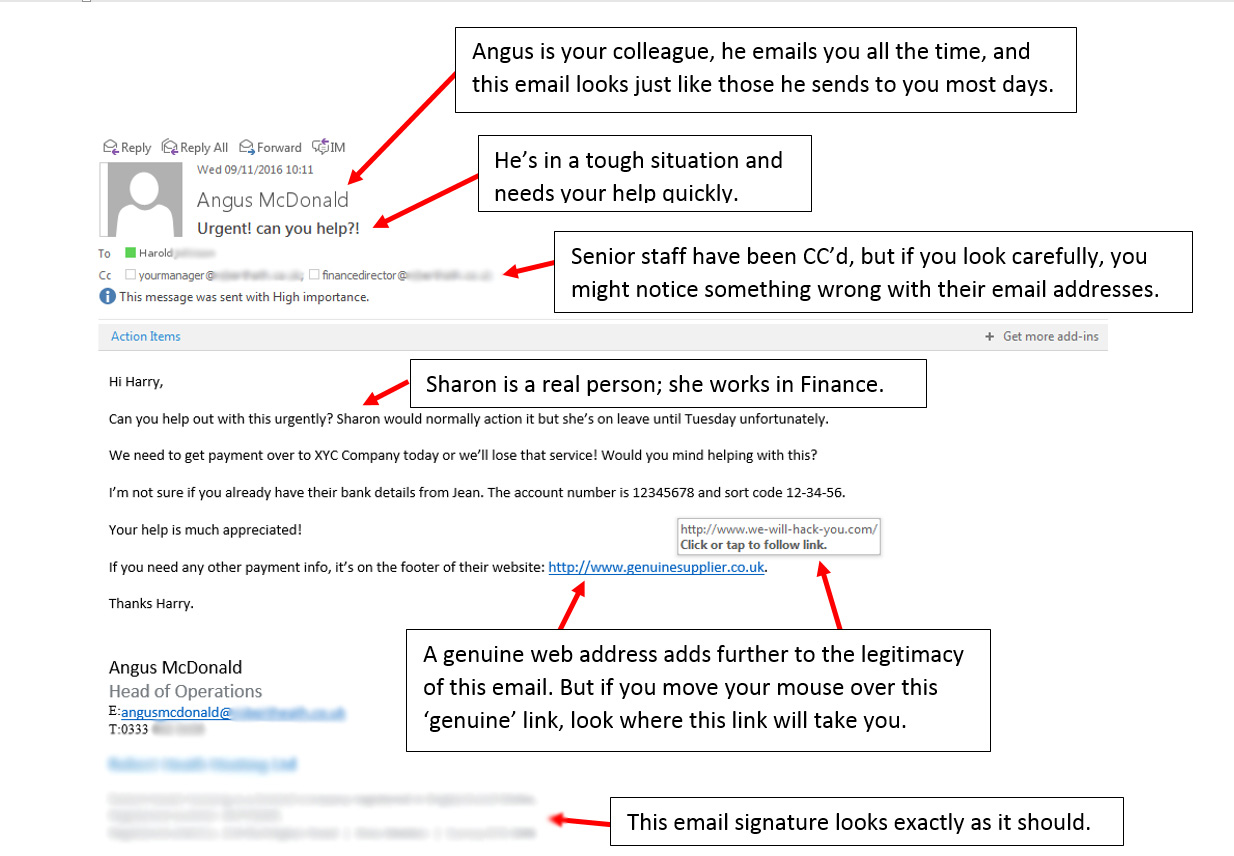
Example: Your colleague emails you to ask you to transfer some money “urgently”. You’re aware that a transfer is due to be made to the person or company mentioned in the message. You’d normally follow a slightly different procedure, but your line manager is away and there’s nobody around you can verify it with face to face. You know that the payment needs to be made quickly to avoid penalties, and helping your colleague seems the right thing to do. You can see that a few senior people were CC’d into the original email, so they’re aware of the situation, and you can see their authorisation in the email history below the request. It all looks above board, but just to be on the safe side, you click ‘Reply All’ to ask if this is genuine. Authorisation comes back from your boss, so you go ahead and make the payment using the account details that your colleague has helpfully included in the email.
What actually happened: A scammer emailed you claiming to be your colleague; they have done their research. They know your colleague’s name and their working relationship to you, and they know the names of a few senior staff members, which they have included in the CC field to make their email appear genuine. They also know that a payment is due to be made to Company X around now, and they know the reasons why it might be urgent for you to do so. The bank details they provided are not for the account they say they are. When you hit ‘Reply All’ to the email to ask your boss if this is okay, you inadvertently email the scammer instead. The scammer, posing as your manager, emails you back to say “yes that’s authorised, please go ahead”.
By the time you receive a spoofed email, the scammer might already have carried out considerable research; for example, on you and your role, on the names and roles of the people you work with, the structure of business etc. Doing this allows them not only to email you posing as someone trustworthy but to do so convincingly.

Persuasion, and intimidation tactics
Sometimes, a scammer will use persuasion tactics to coerce you into doing what they want – you might feel you’re helping a friend or colleague, or doing something in the best interests of the company. Sometimes though, the scammer might decide to use intimidation tactics instead. In these cases, you may be contacted by someone senior. This can be a manager, client, director etc. With intimidation tactics, the main aim is to make you uncomfortable and fearful, and to force you to react to defend yourself. For example, the scammer, posing as someone senior in the company, might make threats and demands e.g. Suggesting that your job is on the line if you don’t perform a certain action immediately.
Impersonating staff/clients
Impersonation, where a hacker impersonates someone familiar, is the cornerstone of almost all social engineering attempts. The impersonation could be of someone within the business, or an outside associate such as an account manager of a service you use. Because of their apparent familiarity, you are much more likely to be inclined to respond to their request. Most of these requests might seem harmless but remember, even if the request is only for information, this could be information which can be used in preparation for a more sophisticated attack.
Hoaxing
Tricking someone into believing that something is real, or false. This is an especially effective technique when the deception is about something urgent or serious, because urgency makes an employee more inclined to bypass proper procedure. For example, creating a false sense of urgency about a false task that must be completed immediately, or there will be serious consequences. The most pernicious of these types of communications will appear to come from someone senior to you, making you even less likely to question or challenge them.
Dumpster diving
Throwing away information incorrectly: on paper, CDs/DVDs, USB sticks, old hard disks, old computers, mobiles, or tablets. All of these media can contain personal information, passwords, information about the internal workings of the company. Skips or outside/kerbside waste containers (“dumpsters”) are favourite starting points for the perpetrators of social engineering-based attacks – this is where they will often begin their research. All of this is valuable information for a hacker, allowing them to better prepare themselves for their main social engineering attack.

Tips
(From our Business IT support)
[sociallocker id=”29352″]
Social engineering exploits can be extremely sophisticated. There are no simple tips for avoiding becoming a victim of one. Nevertheless, here are a few questions to consider which will help you to identify a social engineering attempt:
- Is something of value being requested?
- Does this request fall under my responsibilities? Am I authorised to do this?
- Does my colleague have the authorization to request this from me?
- Is the request particularly pressing or urgent? Does this urgency seem reasonable? Am I tempted to bypass some of the normal procedures because this is so urgent?
- Is this information or action really needed by the requester? Why?
- Does my colleague already have access to this information? Could they do what they’re asking me to do themselves? Why do they need my assistance?
[/sociallocker]
Edit: Check those videos so you can get more examples what Social Engineering is all about.
And check this article: from THE INDEPENDENT.
If you think you might have been contacted by a scammer, you can contact our Business IT support for help:
0333 014 2035
Business IT support open: 7am-7pm, Monday-Friday
Charges may apply
Business IT support provides services to all types of businesses and nationwide.
Our main Business IT support locations: Business IT support Aberystwyth (Wales) and Business IT support Surrey (London).

Author: Pete Gypps
Director of Business Development
Specialisations in transforming SMB and Enterprise businesses from On-Premise Communication products to Cloud Technology.
Let's Start Something new
Say Hello!
Have a project or an idea? You are just a few clicks away from making it a reality.
0333 014 2035
7 Brecon Close, Worcester Park, KT4 8JW
and
10c Science Park, Aberystwyth, SY23 3AH
Ionize has been providing
